Introduction
This article guides you through configuring a Site-to-Site VPN between an AWS Transit Gateway with a VPN attachment and a Palo Alto Firewall. It will also cover exchanging IPv6 routes using BGP to minimize manual effort and control routing advertising using BGP policies. We recommend you use BGP-capable devices, when available, because the BGP protocol offers robust capabilities to assist failover to the second VPN tunnel if the first tunnel goes down.
This guide covers:
- Creating a Customer Gateway on AWS
- Creating an AWS Site-to-Site VPN connection
- Creating a Site-to-Site VPN connection on a Palo Alto firewall
- Creating policy rules that are required to establish a Site-to-Site VPN connection to AWS
- Establishing BGP sessions between your AWS Transit Gateway and a Palo Alto firewall
- Verifying the connectivity between AWS and the Palo Alto firewall across the VPN tunnel
Pre-requisites
- Familiarity with AWS Virtual Private Cloud (VPC), AWS Transit Gateway (TGW), as well as VPC and TGW route tables.
- Familiarity with how the Site-to-Site VPN service handles IPv6 traffic.
- An AWS Transit Gateway configured in your AWS account.
- VPCs with IPv6 CIDR blocks attached to the Transit Gateway.
- Familiarity with BGP. For more information on BGP, please visit this guide.
- A Palo Alto firewall running PAN-OS. This guide was written using Palo Alto firewalls running PAN-OS 10.2.8.
- Palo Alto Firewall interfaces are configured with static and publicly routable IPv4 addresses, assigned to security zones, and assigned to a virtual router. If your firewall requires NAT traversal, please review this Palo Alto Knowledge Base article.
- An on-premises IPv6 subnet
- A default route configured on the Palo Alto firewall pointing to the internet.
Guide Architecture Overview
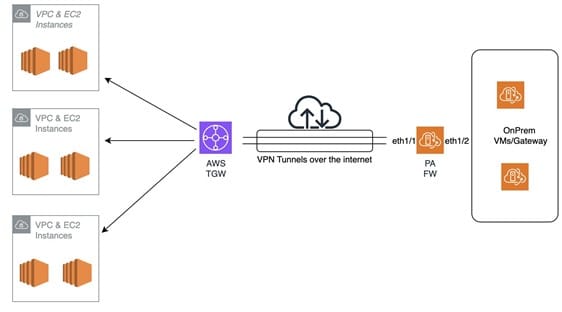
Figure 1: An overview of the architecture used in this guide
The above diagram summarizes the architecture used in this guide. In the guide, we have 3 VPCs in a dualstack configuration with both IPv4 and IPv6 CIDRs. The 3 VPCs are attached to the transit gateway. Each VPC has applications running on port 80 with no access to the internet. The on-premises environment is configured with an IPv6 CIDR block, and the Palo Alto firewall has public IPv4 addresses available for use.
Part 1: Configure the Customer Gateway on AWS console
Navigate to VPC > Virtual Private Network > Customer Gateways
Select Create customer gateway:
- Enter the customer gateway Name tag.
- Enter a BGP ASN (autonomous system number). We are using ASN 65512 for the Palo Alto Firewall (Customer Gateway) and 64512 for the Transit gateway. For more details about using a BGP ASN on with an AWS Site-to-Site VPN, please refer to this guide.
- Enter the Public IP address of the Palo Alto firewall. In this guide, we are using interface Ethernet 1/1 on the Palo Alto firewall. This address must be an IPv4 address.
- In this guide, we will use the pre-shared key method for authentication. Do not select a certificate ARN if you are following this guide. For more details about using certificate-based authentication with an AWS Site-to-Site VPN, please refer to this guide.
- When finished, select Create customer gateway.
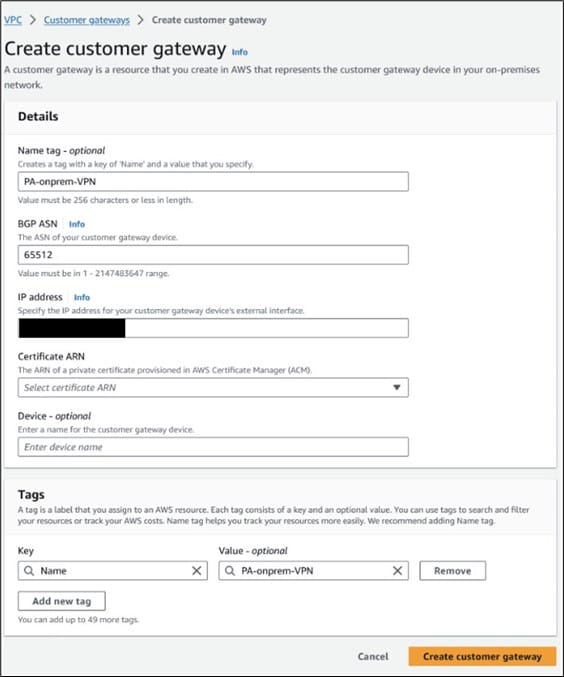
Figure 2: Creating the customer gateway
Part 2: Configure the AWS Site-to-Site VPN connection and associate it with the Transit Gateway
In this section, we will configure the VPN tunnels. AWS recommends using Internet Key Exchange version 2 (IKEv2) where possible, because of the lower overhead in establishing a tunnel and enhanced health check functionality, as compared to IKEv1. For more information on the benefits of IKEv2 with Palo Alto, refer to this guide.
Navigate to VPC > Virtual Private Network (VPN) > Site-to-Site VPN connections
Select Create VPN Connection:
- Enter the VPN connection Name
- Select Transit gateway in Target gateway type and select the desired transit gateway.
- In the Customer gateway section, choose existing and select the customer gateway that was created in Part 1.
- In the Routing options section, choose Dynamic (require BGP).
- In the Tunnel inside IP version, select IPv6.
- Using an Accelerated Site-to-Site VPN connection is out of scope for this guide. For more details, refer to the User Guide.
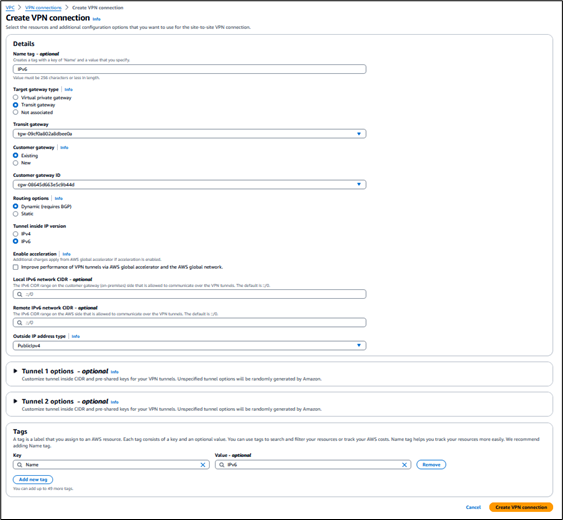
Figure 3: Creating the VPN connection
- Expand the Tunnel 1 and Tunnel 2 options section.
- For the Local and Remote IPv6 network CIDR sections, leave the default ::/0. This will be controlled by firewall policy and routing advertisements, addressed in a later section of this guide.
- Enable the tunnel activity log and tunnel endpoint lifecycle control. AWS Site-to-Site VPN logs provide you with deeper visibility into your Site-to-Site VPN deployments. Site-to-Site VPN connection logs that provide details on IP Security (IPsec) tunnel establishment, IKE negotiations, and dead peer detection (DPD) protocol messages. Tunnel endpoint lifecycle control provides control over the schedule of endpoint replacements.
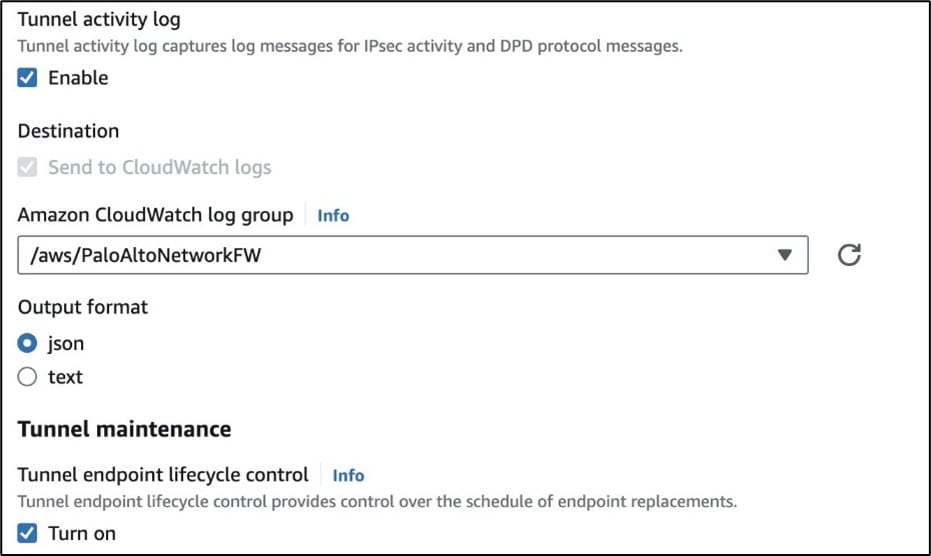
igure 4: Enabling the tunnel activity log and tunnel endpoint lifecycle control
We recommend being more selective with IKE Phase 1 and Phase 2 parameters. These options can be modified by selecting “Edit tunnel (#) options”. Your decisions will depend on your specific compliance and security requirements. For a list of supported parameters, please refer to the VPN tunnel options documentation. Ensure modifications in this section are applied to both VPN tunnels.
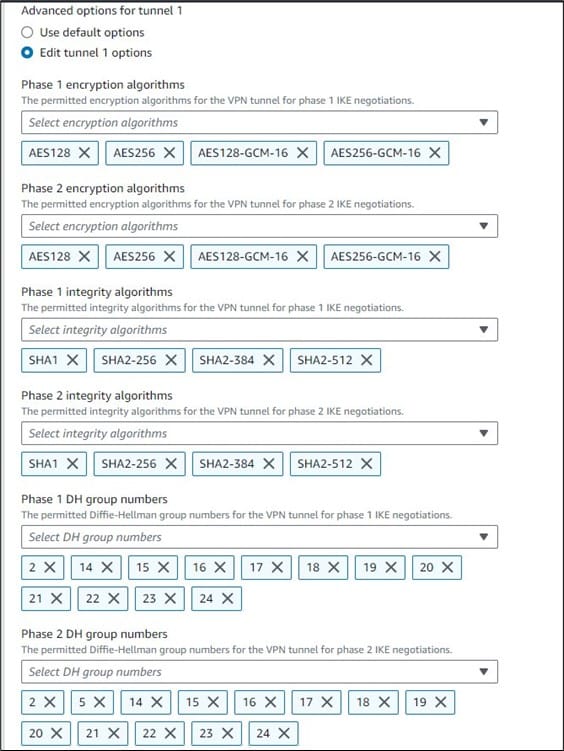
Figure 5: Advanced tunnel encryption options
Encryption algorithms
AWS supports both AES128-GCM-16 and AES256-GCM-16. We recommend AES256-GCM-16 where supported and within requirements.
Integrity algorithms
Integrity algorithms ensure the sender’s identity and also ensure that the message has not been modified in transit. Select your SHA algorithm based on your customer gateway device support and security requirements. If you don’t have specific requirements, then we recommend using SHA-384 because of its performance and security characteristics.
DH group numbers
A Diffie-Hellman (DH) group determines how key material is generated for encryption. As with SHA, we recommend you pick DH groups based on compatibility with your customer gateway device and your security requirements. If you don’t have specific requirements, then we recommend using DH group 20 because of its security characteristics.
IKE version
To establish an IPsec tunnel, the IKE protocol is used. IKE has two iterations: IKEv1 and IKEv2. We recommend using IKEv2, as it gives some key performance optimizations over IKEv1.
For more details on how AWS secures the IPsec tunnel and the shared responsibility model, please refer to this blog post, AWS Site-to-Site VPN, choosing the right options to optimize performance.
After the tunnel creation, a VPN connection summary will be displayed.




















Discussion