"Risk rarely announces itself loudly — but its silence can be deafening when institutional foresight fails."
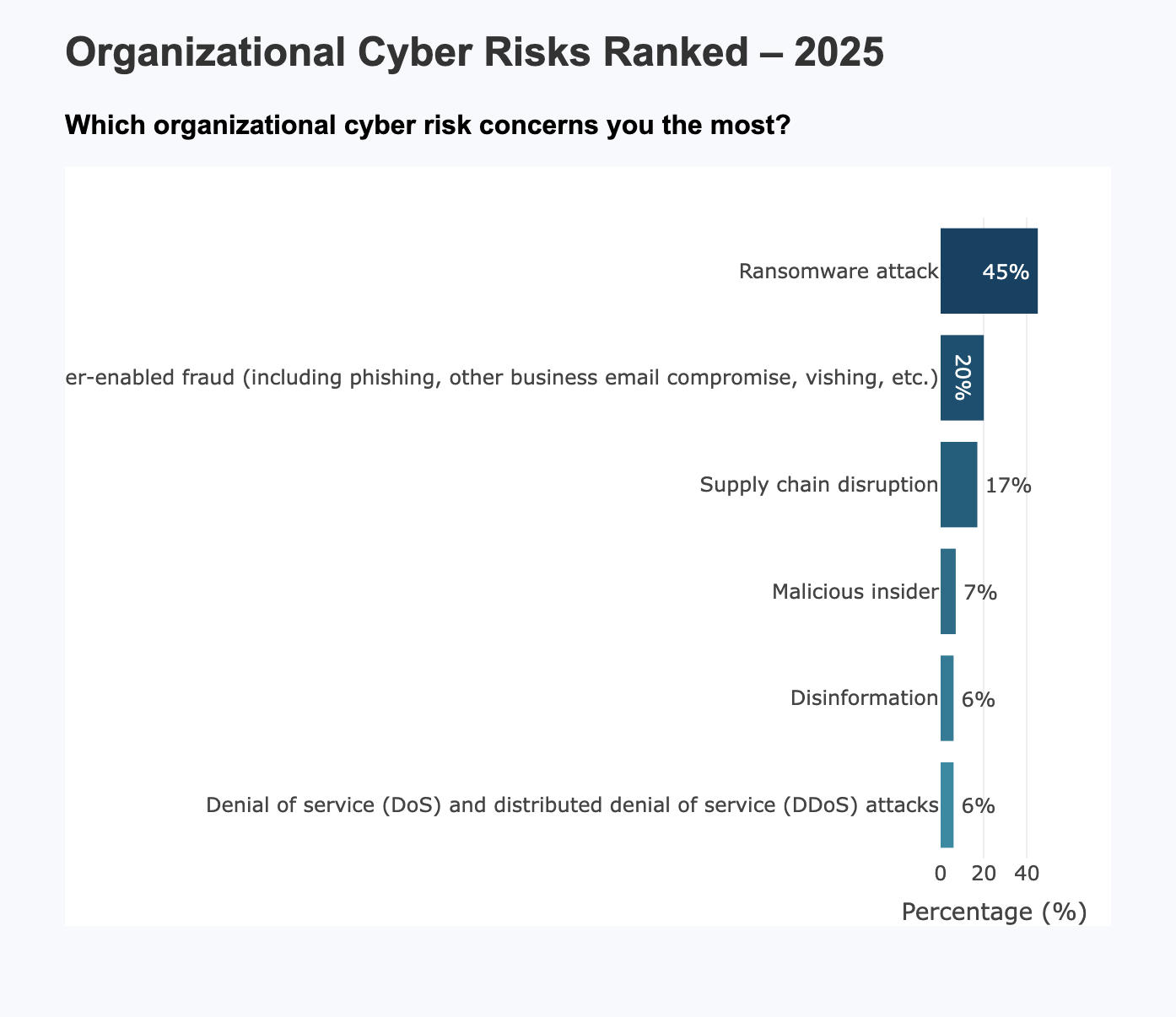
As of 2025, ransomware attacks remain the most dominant concern for organisations across sectors. With 45% of cybersecurity leaders identifying it as their top risk, this figure is no longer merely statistical — it is structural. Ransomware is no longer a technique; it is a business model. And its industrialisation has redrawn the threat landscape.
The Ransomware-as-a-Service Economy: Cybercrime Goes Frictionless
In recent years, ransomware has undergone a fundamental operational shift. What was once the domain of highly skilled attackers has evolved into a commoditised service available via subscription-based platforms. The Ransomware-as-a-Service (RaaS) ecosystem has lowered the barrier to entry, expanded the diversity of threat actors, and dramatically increased attack velocity.
The implications are sobering:
- Sophistication no longer correlates with attacker profile
- Disruption is now decoupled from technical capability
- Recovery timelines are extended not due to complexity, but due to scale and simultaneity
2026–2030: Strategic Forecasts for a Volatile Digital Decade
As organisations pivot from perimeter defence to operational resilience, the coming years will test the agility of cybersecurity governance models in ways previously unimagined. Below is a forward-looking analysis of the evolving threat landscape:
2026: The Hybridisation of Hostility
AI-enhanced ransomware campaigns will rise sharply. Payloads will adapt dynamically to behavioural patterns within the target environment. Deepfake voice messages, synthetically generated emails, and executive impersonation will become standard components of the attack lifecycle.
2027: Supply Chains Under Siege
Threat actors will increasingly target supplier ecosystems instead of enterprise networks. The exploitation of third- and fourth-tier vendor vulnerabilities will become prevalent. Organisations will require real-time cyber risk ratings for their suppliers—comparable to credit scoring models—to preserve trust and operational continuity.
2028: The Era of Ransom-Theatre
Extortion will evolve beyond data encryption. Adversaries will launch parallel disinformation campaigns aimed at shareholders, regulators, and media outlets. Public perception will become as valuable a hostage as company data. This convergence of narrative warfare and cyberattack will usher in the era of “extortion as performance.”
Enterprise Response: From Firewalls to Foresight
Ransomware must no longer be viewed solely as an IT concern. It is a board-level risk with legal, reputational, and financial implications. Forward-thinking organisations should implement:
- Cyber crisis simulations involving executive leadership
- Behavioural threat detection beyond technical signature-based tools
- Immutable backup architectures with autonomous recovery mechanisms
- Embedded cyber trust scoring within procurement processes
In this context, resilience means more than recovery—it means strategic anticipation.
The Core Truth: Ransomware Is a Symptom, Not the Disease
To view ransomware solely as a threat vector is to miss the wider point. It is the result of fragmented defences, unregulated tooling ecosystems, and the widening gap between policy and implementation.
Looking towards 2030, the most resilient institutions will not be those that block every threat, but those that endure, absorb, and adapt faster than their adversaries evolve.
The age of static controls is over. This is the decade of adaptive resilience.




















Discussion